AoCyber: Side Quest 3 Part 0
TL;DR: Un-Acropolypse the cropped image from the chat conversation.

If you found this post you probably already found this room: https://tryhackme.com/room/busyvimfrosteau
See this years' other rooms as well:
SQ 1: Day 0
SQ 2: Day 6
SQ 3: Day 11
SQ 4: Day 20
Index of this challenge:
Finding this puzzle was probably the most difficult for me as I have very little experience around end-user systems and probably an insufficient amount of exposure to Windows Active Directory. But none-the-less: Here I find myself needing to get through this hurdle to get to the next challenge.
Day 11
Again, the main event is outside the scope of these articles, the daily activity itself has a great writeup and instructions. We'll start off after the target flag was captured, at the hint for our room:
"Van Sprinkles left some stuff around the DC. It's like a secret message waiting to be unraveled!"
In this case, DC is Domain Controller, the host that our users are on. Shame on them!
In the same folder that the flag resides is mysterious chat files. With Evil-WinRM I simply did a Compress-Archive and download command of the desktop so I could browse to the chat log.
*Evil-WinRM* PS C:\Users\vansprinkles> Compress-Archive ../Administrator/Desktop admin
*Evil-WinRM* PS C:\Users\vansprinkles> ls
Directory: C:\Users\vansprinkles
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 11/14/2018 6:56 AM Desktop
d-r--- 11/15/2023 9:29 PM Documents
d-r--- 9/15/2018 7:19 AM Downloads
d-r--- 9/15/2018 7:19 AM Favorites
d-r--- 9/15/2018 7:19 AM Links
d-r--- 9/15/2018 7:19 AM Music
d-r--- 9/15/2018 7:19 AM Pictures
d----- 9/15/2018 7:19 AM Saved Games
d-r--- 9/15/2018 7:19 AM Videos
-a---- 12/11/2023 4:51 PM 1667881 admin.zip
do*Evil-WinRM* PS C:\Users\vansprinkles> download admin.zip
Info: Downloading C:\Users\vansprinkles\admin.zip to admin.zip
Info: Download successful!
With a quick python3 -m http.server --bind 0.0.0.0 9000 I had it open in my browser to look at it the way it was intended.
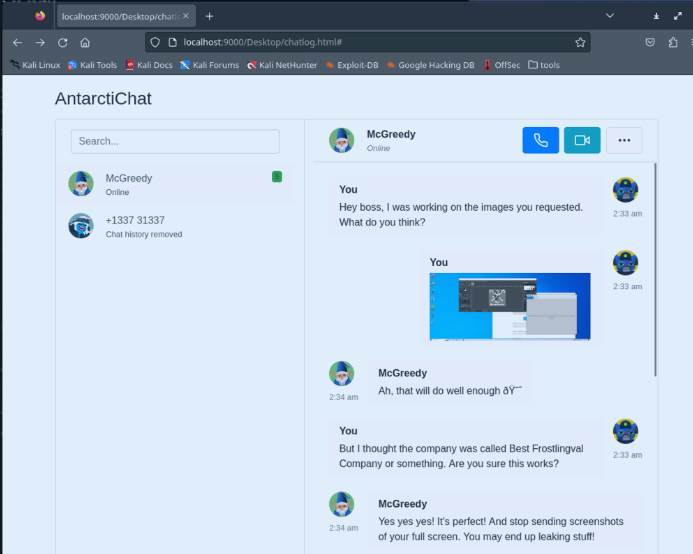
McGreedy is complaining about full screen snapshots that might leak valuable data. And even goes into deleting an image and sending a cropped version of it using "Snip & Sketch", the Windows 11 default screen clipping tool:
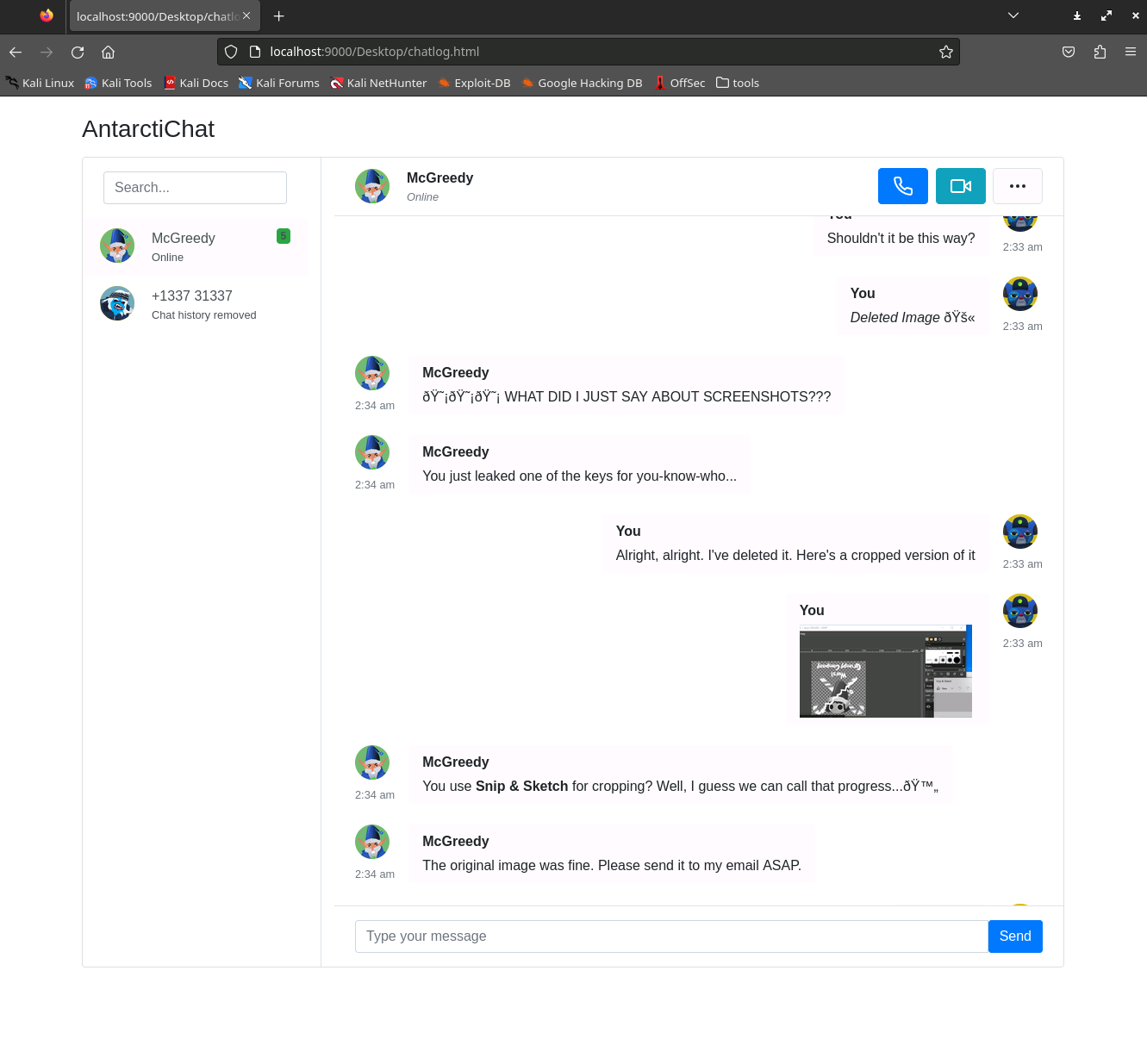
I'll admit, my first inclination was to look up the app and see how it runs. I found a great stack overflow article talking about how it aggressively saved cached images forever in the %LocalAppData% folder. I tried to access it and was hit with a permission denied. In fact, every folder OTHER than the desktop basically lead to this.
After spending about 20-30 minutes looking up Windows AD privilege escalation techniques, a vulnerability for the application that had nothing to do with AD was brought to my attention.
"Acropolypse". Apparently some applications cropping images leave the cropped file in a state where the removed image can be brought back if you know the app and the resolution to plug into a tool like https://github.com/frankthetank-music/Acropalypse-Multi-Tool
Using the full screenshot to find the resolution of the cropped image, and plugging in Windows 11: You're presented with a neat snapshot of the QR code to: